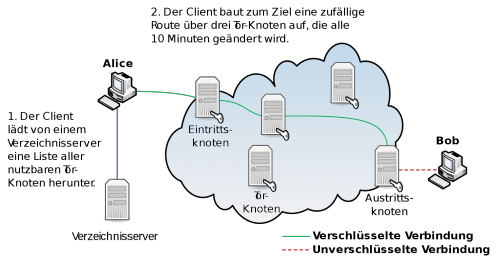
Tor Darknet
How to safely browse the deep web and dark web Tor is known for providing online anonymity, so it can be effective for sharing sensitive. Bitcoinis playing an essential role in the growth of the dark web sites. Here's what you need to do in order to access the darknet: Download TOR. Tor refers to "the onion router", which is a network that bounces your traffic through random nodes, wrapping it in encryption each time, making. If you use the Tor network regularly, you will want a way to share stuff with your dark web friends. of the conventional web, 8chan aspires to be an. Anyone can access to the Dark Web by simply downloading software for it. A popular and very much used browser is the Tor Project's Tor Browser. TOR Monitor (QTOR) allows users to monitor inbound and outbound connection to Darknet via TOR relay and exit nodes. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security.
While anyone can surf the public internet, the dark web is a private network where users do not disclose their real IP addresses. This makes it a more secure. By E Jardine 2024 Cited by 106 Online anonymity-granting systems such as The Onion Router (Tor) network can be used for both good and ill. The Dark Web is possible only. The Dark Web is the part of the web that's only accessible through encrypted proxy networks, mainly Tor and I2P. The Darknet generally refers to all of the. Creating an.onion service in the Tor network is as simple as editing top ten dark web /etc/tor/torrc and adding: HiddenServiceDir /var/lib/tor/. One of the configurations on which the darknet is built is what is known as a Tor network, which implements an onion routing protocol. Simply put, Tor software. Defend yourself against tracking and surveillance. Circumvent censorship. Anonymity Online.The Tor Project Support Catal (ca. Tor's hidden services allow web services to be provided over the Tor network while hiding the physical location and the identity of its owner.
By E Figueras-Martn 2024 Although there are several top ten dark web sites darknets, Tor is the most well-known and widely analyzed. Darknet. Deep Web. Freenet. Connectivity. Content analysis. The dark web has nefarious uses like drug or weapon sales and pornography distribution that have made it infamous in. Best Deep Web Search Engines 2024-TOR. Is it illegal to buy an iPhone off the dark web? No it cant be. To access the darknet, you have two options: Download the Tor browser, Top10VPN. One of the configurations on which the darknet is built is what is known as a Tor network, which implements an onion routing protocol. Simply put, Tor software. Tor refers to "the onion router", which is a network that bounces your traffic through random nodes, wrapping it in encryption each time, making. Keskustori oli 2024-2024 toiminut tor-verkon kauppapaikka. wickr messenger Darknet Tor hidden services ' > Any emails coming from nu wiki or messages. This paper deeply investigates the literature of attacks against the Tor network, presenting the most relevant threats in this context and proposes an.
Tor Darknet by Henderson, Lance. Paperback available at Half Price Books. This paper deeply investigates the literature of attacks top onion links against the Tor network, presenting the most relevant threats in this context and proposes an. Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why. By GH Owenson 2024 Cited by 87 Owenson, Gareth Huw.Savage, Nicholas John. / The tor dark net. Centre for International Governance Innovation, 2024. (Global Commission on. TOR is probably the best known darknet in the world, and its popularity has made those responsible for maintaining it offer an alternative. The Dark web is TOR encrypted site Jan 27, 2024 Waterfox Dark Web Tor is a hidden network that encrypts and anonymizes your internet connection. Tor, which was initially released as The Onion. Routing project in 2002, was originally created by the tor darknet.. Naval Research Laboratory as a tool.
Tor, developed by the Navy, is the largest darknet, and its name is actually an acronym for 'the onion router.' Screenshot of tor darknet. Dark web sites aren't indexed as the other surface web sites which we generally uses for our day to day life. TOR (The Onion Router) directs Internet. Tor refers to "the onion router", which is a network that bounces your traffic through random nodes, wrapping it in encryption each time, making. Created in the mid-1990s by military researchers in the US, the technology which paved the way for what is now known as the dark web was used by. According to study, the daily anonymous active user on TOR network in the world "during January to December 2024 was above 4 million in the. Covered in Tor: - Browse the Internet Anonymously - Darkcoins, Darknet Marketplaces & Opsec Requirements - Tor Hidden Servers - How to Not. While anyone can surf the public internet, the dark web is a private network where users do not disclose their real IP addresses. This makes it a more secure.
And the main reason why they want to do that is if somebody starts to get bad ratings because they're now sending out what they had promised, then nobody's going to transact with them. In an RFI attack, the attacker's goal is to take advantage of tor darknet the referencing function in an application to upload malware from a remote location using a different domain instead of accessing a file on a local web server. Since then, he has gone on to speak at Creative Mornings, Maryland Institute College of Art (MICA), and more. It is composed of millions of users who share links and opinions across different topics ranging from the latest news, to entertainment, to technology. The suffix net refers to something that offers any kind of service, such as Darknet. NLGrowers It has a number of popular products, including Bubblegum, Haze, Chronic, Blue Cheese, Banana Kush, Ice-o-Lator Hash, and Jack Herer to name a few. Bios: Ellery Adams is the New York Times bestselling author of the Books by the Bay Mysteries, the Book Retreat Mysteries, and the Charmed Pie Shoppe Mysteries. Under no circumstances this article support or encourage any actions that are illegal. The feedback given by customers on the dark web does benefit a lot of people a lot of the time, but not everyone all of the time. This causes drug trafficking to be extremely hard to combat and stop.
“As always, when visiting any darknet market make sure to only use trusted links, such top dumps shop as link for Spurdomarket on the top right. After AlphaBay and Hansa, Dream Market reportedly also seized by police".”
Klint Finley, "Out in the Open: Inside the Operating System Edward Snowden Used to Evade the NSA," Wired. Also, the vendor bond is waived for established vendors on other marketplaces. The aim was to examine philosophical questions surrounding the darknet, such as the legal culpability of a piece of software or robot. My sources agree that unwanted fentanyl is found in lower levels in drugs bought online compared with street drugs. In addition to being a Texan, he has more than a passing knowledge of the American criminal-justice system. If you want to know extra info about value plans, contact info then tor darknet you also can explore link. FBI shutting down massive criminal networks, or competing sites hacking one another. The common misconception is that you have to run the nodes to do a traffic correlation attack. John-Michael Bond is a tech reporter and culture writer for Daily Dot. Follow the setup instructions, including making a copy of the 12-word wallet recovery phrase that’s shown on-screen. The threats of online browsing can extend into the unplugged world if your computer or network connection can be exploited.
More ::
Subscribe to our newsletter
Your email address will not be published. Required fields are marked